Two highly effective botnets have been dismantled by regulation enforcement businesses and the alleged directors now face prison costs, U.S. prosecutors mentioned Friday.
The Justice Division said it seized the domains Anyproxy.internet and 5socks.internet — with each websites now that includes a regulation enforcement takedown banner. The banners say the web sites have been disrupted in an operation known as “Moonlander.”
Three Russian nationals — 37-year-old Alexey Viktorovich Chertkov, 41-year-old Kirill Vladimirovich Morozov and 36-year-old Aleksandr Aleksandrovich Shishkin — have been charged with conspiracy and harm to protected computer systems for his or her function in operating botnet companies provided by means of Anyproxy and 5socks. Kazakhstani nationwide Dmitriy Rubtsov, 38, was hit with the identical costs.
The Justice Division didn’t say the place the lads are at the moment based mostly.
The 4 created the botnets by infecting older-model wi-fi web routers within the U.S. and overseas. A malware marketing campaign allowed the lads to reconfigure the routers and supply them on the market as proxy servers by means of the Anyproxy and 5socks websites.
The 5socks.internet web site provided greater than 7,000 proxies on the market and allowed customers to pay month-to-month charges of as much as $110 for entry.
The Justice Division mentioned the web site domains have been managed by an organization based mostly in Virginia and that the 4 males allegedly earned about $46 million by means of the contaminated routers over a 20-year stretch.
The discover coincides with an alert released by the FBI on Wednesday warning those who end-of-life routers which might be not supported by the businesses that made them have been the first goal of the directors behind Anyproxy and 5socks.
The advisory notes that Chinese language cyber actors “are additionally amongst those that have taken benefit of identified vulnerabilities in finish of life routers and different edge units to determine botnets used to hide hacking into US crucial infrastructures.”
The routers listed within the advisory embrace older fashions from Linksys or Cisco.
Chertkov and Rubtsov have been slapped with further costs of false registration of a website identify after they used pretend identities to register the domains.
The investigation was run out of the Oklahoma Metropolis FBI workplace after a number of companies and houses within the state have been discovered to have routers contaminated with the malware used within the marketing campaign.
U.S. officers labored with regulation enforcement in Thailand and the Netherlands on the operation in addition to Lumen Applied sciences’ Black Lotus Labs. The corporate posted a technical analysis of the operation on its weblog, reporting that it tracked a “weekly common of 1,000 distinctive bots involved with the command-and-control (C2) infrastructure, situated in Turkey.”
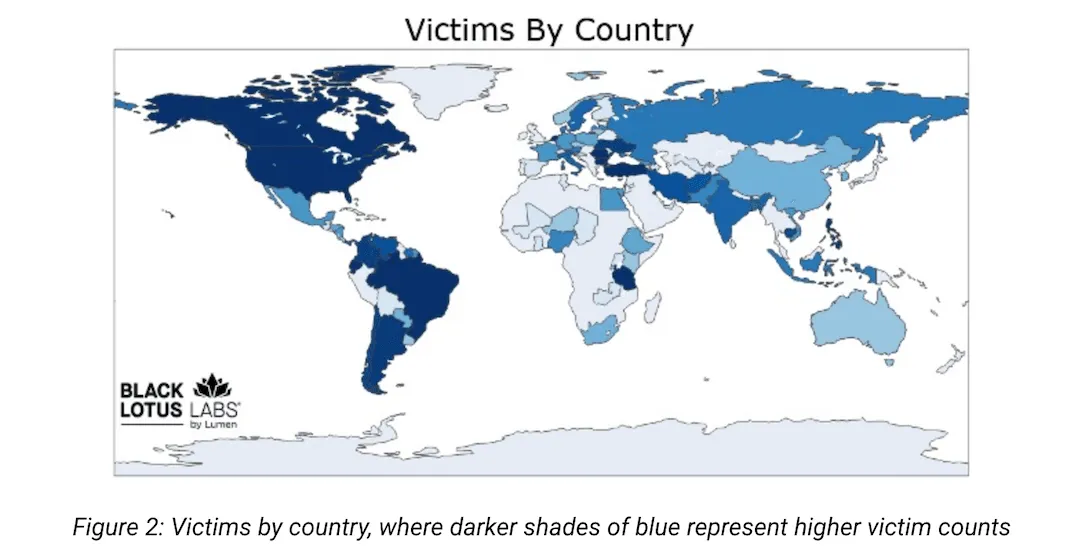
Black Lotus Labs’ map exhibiting the focus of botnet victims.
“Over half of those victims are in america, with Canada and Ecuador exhibiting the following two highest totals,” the researchers mentioned. “Primarily based on Black Lotus Labs’ telemetry, we are able to see a mean of about 1,000 weekly lively proxies in over 80 international locations, nonetheless we imagine their true bot inhabitants is lower than marketed to potential customers.”
The operation was initially found by CERT Orange Polska in 2023 and Lumen spent a couple of 12 months monitoring it. Lumen discovered that the group just isn’t utilizing zero-day vulnerabilities and sometimes exploits an array of bugs to take over units — particularly focusing on end-of-life units with points courting again years.
The FBI urged individuals to learn by means of its advisory to see if their model of router was impacted and substitute it with a brand new mannequin. Customers can even reboot the gadget and disable distant administration.
Compromised routers proceed to be a key avenue for Chinese language hacking campaigns focusing on U.S. crucial infrastructure. U.S. officers in current months have raised alarms about TP-Link routers particularly as a result of they’re repeatedly being exploited by Chinese language hackers who’ve used them to breach telecommunications giants.
For years, crucial vulnerabilities in routers have been abused by hackers who use them as cowl for subsequent assaults or add them to powerful botnets that disrupt web sites with bogus site visitors.
Recorded Future
Intelligence Cloud.






